By Quentin Halsey
- July 10, 2023
In our digital era, where businesses are more connected than ever, the unfortunate reality is that cyber threats are a growing concern. Phishing emails and a variety of other cyber-attacks are causing increasing harm to businesses worldwide. For those not deeply involved in the world of technology, these terms can sound like technobabble, so let’s break them down.
What Are Phishing Emails?
At its core, phishing is a form of deception. It’s an online scam where attackers send an email that appears to be from a trustworthy source to trick the recipient into providing sensitive data. This data often includes personal information like credit card numbers or login credentials to important websites. The phishing email may ask you to confirm personal details or might even contain a link to a website that looks legitimate but is designed to capture your information when you try to log in.

Phishing attacks have become increasingly sophisticated. Attackers are now using social engineering methods and personalized emails to make their scams more convincing, a technique known as spear-phishing. They might gather public information about you or your business from social media and other online platforms to craft emails that seem to come from familiar sources.
Other Common Cyber Attacks
Phishing isn’t the only threat out there, though. Here are a few more types of common cyber-attacks:
- Ransomware: This is a type of malicious software that encrypts a victim’s files. The attacker then demands a ransom from the victim to restore access to the data upon payment.
- Malware: This is any software intentionally designed to cause damage to a computer, server, client, or computer network. Malware might be delivered in an innocuous-looking email attachment or even hidden on a website.
- DDoS Attacks: Short for Distributed Denial of Service, these attacks work by flooding a website or online service with so much traffic that it can’t cope and crashes, denying service to legitimate users.
- Man-in-the-Middle Attacks (MitM): These occur when attackers secretly relay and possibly alter the communication between two parties who believe they are directly communicating with each other.
The Rising Threat
Unfortunately, cyber threats have been on the rise in recent years. As businesses become more interconnected and rely more heavily on online services, cybercriminals have taken advantage. They’ve become more sophisticated, and their attacks have grown more harmful.
Phishing attacks have seen a significant rise. According to the FBI’s Internet Crime Report, the total cost of internet crime in 2020 was over $4.2 billion, with phishing scams accounting for $54 million of that. And it’s not just about the financial loss. A successful cyber-attack can damage a company’s reputation, cause loss of data, and lead to significant downtime.
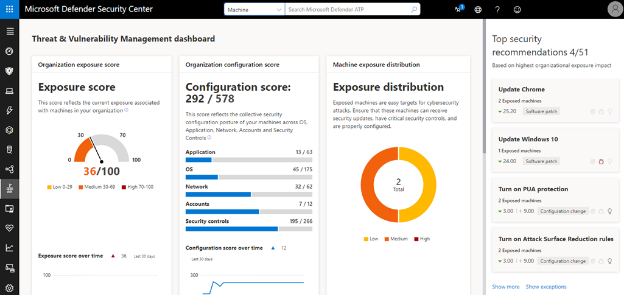
In the increasingly interconnected digital landscape, it is crucial to ensure that your business is well-protected against the ever-growing range of cyber threats. This is where Microsoft Defender steps in. Formerly known as Windows Defender, this integrated security solution serves as a robust line of defense against a wide variety of security vulnerabilities.
Without the aid of an integrated security solution like Microsoft Defender, the responsibility of detecting and thwarting phishing attempts falls onto the user. This often means having to vigilantly scrutinize every email you receive – a time-consuming process that might detract from your productivity. Here’s a look at the steps involved:
- Careful Examination of Email Addresses: One common sign of a phishing email is a suspicious email address. It might look similar to a familiar email, with perhaps one or two letters off – just enough to trick acasual observer. Without an automatic system, you need to check each email address carefully to ensure its legitimacy.
- Scrutinizing Links: Phishing emails often contain links to malicious websites designed to steal your information. To protect yourself, you should never click on a link in an email unless you’re certain it’s safe. This means you’ll need to hover over each link to see the actual URL before clicking, an especially time-consuming task.
- Checking for Spelling and Grammar Errors: While not always the case, phishing emails often contain spelling and grammar errors. This means you should be on the lookout for these mistakes as potential signs of a phishing attempt.
- Investigating the Email’s Tone and Requests: Phishing emails often create a sense of urgency or demand immediate action. This can be a red flag. However, it requires careful analysis of each email’s content, another time-consuming task.
- Verifying Attachments: Attachments can carry malware. Therefore, unless you’re expecting an attachment and are sure of the sender’s identity, you should be wary of any unsolicited attachments.

While these precautions are all valuable and important, they also highlight the significant effort required to manually protect yourself from phishing attempts. For busy professionals, this can represent a considerable amount of time and energy spent on a task that could be automated.
This is where Microsoft Defender can be a game-changer. It offers an efficient, reliable, and automated solution to these threats, freeing you from the burden of having to carefully examine every single email, link, and attachment you receive. This allows you to focus on what truly matters – growing and managing your business.
As such, enabling Microsoft Defender can represent a significant step toward creating a safer, more secure digital environment for your business, offering peace of mind amidst the rising tide of cyberthreats.
Comprehensive Protection
Microsoft Defender offers a comprehensive set of protections against common cyber threats. Here’s how it protects your business:
- Anti-Malware Capabilities: At its core, Microsoft Defender is an antivirus program, providing real-time protection against software threats like viruses, malware, and spyware across email, apps, the cloud, and the web. It scans for malicious threats in real-time, helping to shield your systems before potential damage can occur.
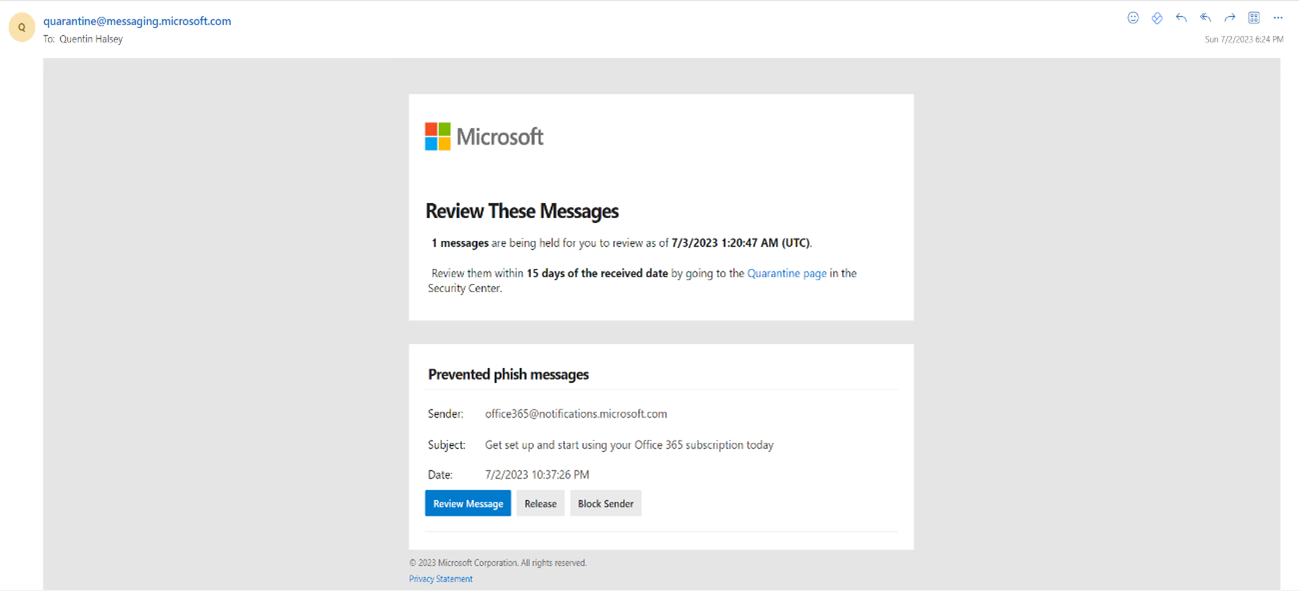
- Anti-Phishing: Microsoft Defender SmartScreen is specifically designed to guard against phishing sites by checking web pages against a constantly updated list of reported phishing sites. It also checks downloaded files and web content, blocking known-dangerous content.
- Network Protection: Defender provides network protection, extending the SmartScreen capabilities to block all outbound processes on the device against dangerous sites, even non-Microsoft browsers.
- Ransomware Protection: Defender’s Controlled folder access prevents ransomware and other unwanted apps from making unwanted changes to your files, helping to keep your data safe.
- Email Protection: Defender’s integration with Microsoft 365 means it scans your email for malicious links and attachments, providing a crucial layer of security where phishing attacks often occur.
Seamless Updates
One of the great benefits of Microsoft Defender is that it’s fully integrated into Windows 10/11 and is updated regularly with the latest malware definitions through Windows Update. This ensures your defenses stay updated to handle the latest threats without needing to manually update your systems.
Accessibility and Ease of Use
Finally, Microsoft Defender is user-friendly and designed for non-tech professionals. It operates seamlessly in the background, not requiring constant monitoring or complicated set-up procedures. However, it still offers customizable controls for businesses that wish to fine-tune their security settings.
In conclusion, Microsoft Defender offers an accessible, easy-to-use solution that provides comprehensive protection against a wide array of cyber threats. As the digital landscape continues to evolve, using tools like Microsoft Defender is vital in maintaining the security of your business.
Remember, no security system is entirely foolproof, so it’s important to follow best practices for online safety, such as regularly updating software, backing up data, and educating employees about the risks of phishing and other cyber-attacks.
The most common way people give up their power is by thinking they don’t have any.

